Home | Ecosystems | SAP | Market Leader in Zero Trust Security for SAP
Market Leader in Zero Trust Security for SAP
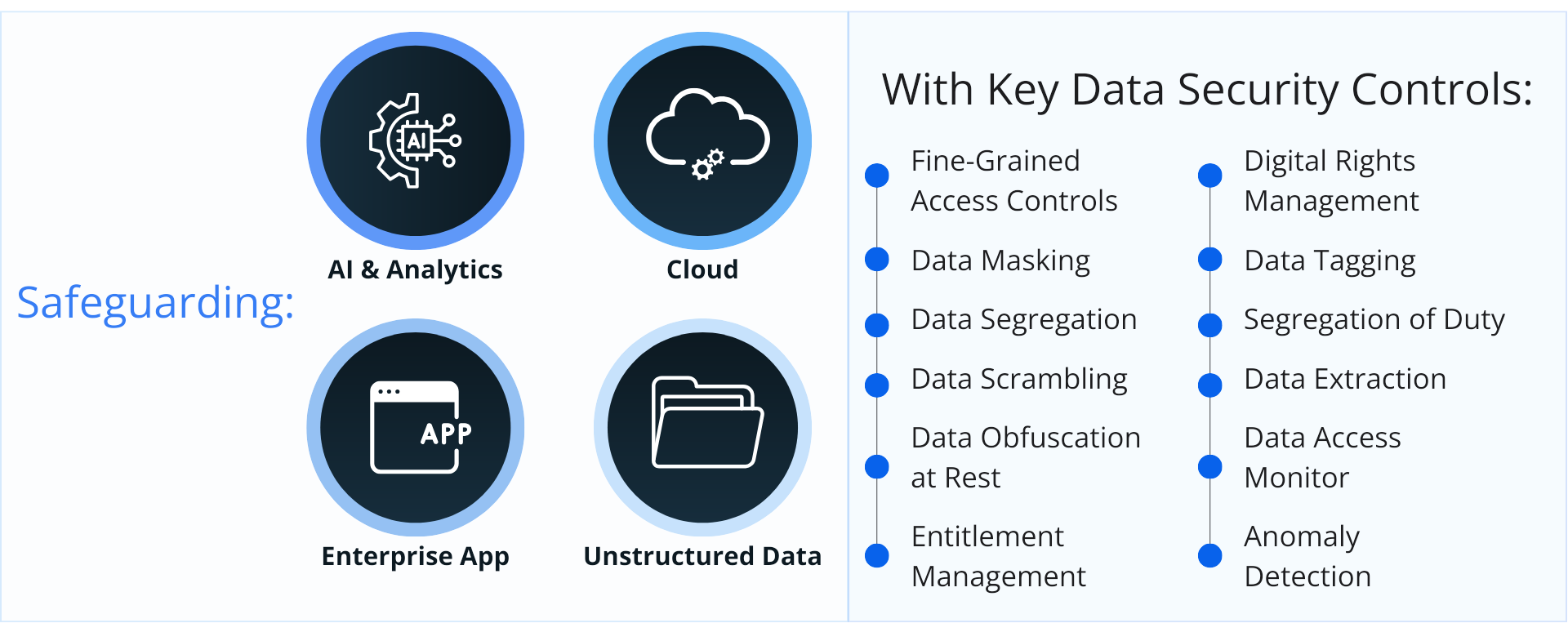
Set the standard for safeguarding data across all ecosystems
Home | Ecosystems | SAP | Market Leader in Zero Trust Security for SAP
Set the standard for safeguarding data across all ecosystems
SAP is at the forefront of today’s digital landscape, serving as the backbone for many enterprises’ core processes and operations. Its array of applications and services not only streamlines data management and resource planning, but also fosters enhanced decision-making and operational efficiency. As reliance on this integrated platform intensifies, the imperative to safeguard it becomes increasingly critical.
Recognizing the criticality of these systems, NextLabs partners with SAP to provide zero trust data-centric security (DCS) solutions, crafted to align with SAP’s unique ecosystem.
SAP transactions secured per year

SAP users protected

SAP business objects secured

Top 100 SAP customers protected

SAP applications secured
How do enterprises thrive through constant change? This question plagues many executives as they face unprecedented disruption to their business environment. With the rise and rapid adoption of generative AI, cloud computing and digital transformation, technology has become the most disruptive force for businesses today.
This strategic shift towards reinvention, fueled by Gen AI, has created an enormous need for a digital core. A digital core enables organizations to accelerate ahead of the competition and achieve their ambitions—using the right mix of AI, big data & analytics, ERP, unstructured data, and cloud computing. However, at the same time it is critical to design security at every level.
When factoring in Zero Trust Data Security in at each level, it enables enterprises to secure their entire digital core or application ecosystem. By controlling access, safeguarding the data itself, protecting data in use, and safeguarding outputs, enterprises can protect their ecosystem, maintain operational integrity, and foster trust in new technologies. Explore below how this is achieved:
Whether it be AI systems, ERP systems, data analytics, or cloud infrastructure, it is critical to control access to the system in which sensitive data resides. Given the Zero Trust Architecture (ZTA) emphasizes the principle of “never trust, always verify,” it ensures every request to access critical systems are authenticated and authorized, regardless of its origin.
With the implementation of dynamic authorization, attribute-based access controls (ABAC), and continuous monitoring, enterprises can significantly reduce the risk of unauthorized. By ensuring that every request is verified, enterprises can prevent malicious actors from exploiting or extracting information from critical systems for harmful purposes. Additionally, the use of the least privilege principle ensures that users and processes only have access to the resources necessary for their job function, making it easy to enforce segregation of duties (SoD), and minimizes the attack surface and prevents breaches.
Data related to an enterprise’s digital core, despite its diversity, serves as the engine that drives innovation within the organization. If it is not adequately protected, it becomes vulnerable to insider risks and a prime target for cyberattacks.
Some proven techniques used to apply controls to protect data are data tagging, encryption, dynamic data masking, and logical segregation, which are essential for maintaining the integrity and confidentiality of data. Data tagging helps in identifying and categorizing data based on its sensitivity, enabling tailored security measures. Encryption secures data by converting it into an unreadable format, while dynamic data masking changes the data stream so that the data requester does not get access to the sensitive data with no physical changes to the original production data. Data segregation partitions sensitive information virtually via policy to allow only authorized users to view the data sets that pertain to them.
Developing trust-based mechanisms that establish high levels of trust in the data source and separately in the trustworthiness of the data allows enterprises to align appropriate data use with business goals, both within and outside the organization. Due to this, it is critical to protect data throughout its lifecycle – at the source, at the point of use, and on the move — during collection, use, analysis, processing, and transmission.
Fine-grained access controls and entitlement management can effectively restrict access and segregate sensitive data at its source, ensuring that only authorized users can access and share information. Dynamic data masking, scrambling, and obfuscation techniques can protect data in use by rendering sensitive information unrecognizable to unauthorized users at the point of access, while encryption safeguards data in transit. When these techniques are implemented effectively, enterprises can enhance data governance and prevent the leakage of sensitive information throughout its lifecycle.
Organizations that promote data sharing among employees, partners, and stakeholders have outperformed their peers on most business value metrics. To balance collaboration and security, enterprises need a solution that maintains data protection regardless of how or with whom it is shared, preventing unauthorized transfers and improper sharing.
Enterprise Digital Rights Management (E-DRM) protects sensitive information throughout its lifecycle from unauthorized access, use, and distribution. E-DRM employs attribute-based policies to dynamically grant permissions based on the recipient’s identity for specific actions—such as viewing, editing, copying, forwarding, printing, and extracting content—with options to set expiration dates, dynamic watermarks, and usage limits. Policies can be updated or revoked even after a document is shared outside the enterprise. E-DRM provides peace of mind for safe file sharing with internal and external stakeholders while mitigating risks of unauthorized access and breaches.
Explore NextLabs and SAP’s combined resources to learn about their joint solutions that are being used by industry leaders to safeguard business-critical data.

For success in today’s hyperconnected world, your users and business partners need 24×7 access to any data on any device. How can you share data to keep them informed while still protecting trade secrets and intellectual property?
Discover how SAP® Enterprise Digital Rights Management application by NextLabs (also known as SkyDRM for SAP) is helping enterprises persistently protect their sensitive data regardless of where it travels.

Businesses that support collaboration beyond their boundaries benefit greatly from improved innovation and productivity. But how do you enable your employees and partners to access and share enterprise data without compromising security? How can you work closely with partners and an extended supplier network to design and manufacture best-in-class products?
Explore in this solution paper how NextLabs Application Enforcer for SAP helps you achieve this balance, maximizing your existing investment in SAP applications.
Enforces data-level security controls – such as field-level data masking and record–level data segregation, and monitors data access activity directly from within the data access layer of the SAP S/4 HANA and SAP ECC. DAE for SAP ERP Enterprise Edition also supports Format Preserving Encryption (FPE) of data at rest in the database.
Enables organizations to add yet another layer of protection for sensitive and confidential data in ECC and S/4HANA.
Applies digital rights protection to ensure persistent protection of critical information throughout its lifecycle with proper level of security controls. With SkyDRM for SAP, this level of protection is integrated natively with SAP Business Suite to ensure that data extracted or taken out of SAP applications is continually protected.
Works with SAP GTS to manage the export of technical data. Together, Application Enforcer and Technical Data export Compliance (TDEC) provide an end-to-end solution for export compliance, addressing the export of physical goods, digital goods and technical data.
Works with the SAP Access Control application to extend role-based access control using attributes about the user, the data and the environment. It enables customers to enforce business authorizations with fine-grained controls to ensure only authorized users have access to confidential information.
Enables organizations to prevent data loss or leakage from SAP ECC and S/4HANA.
NextLabs works closely with system integration partners to deliver high-value solutions based on NextLabs technologies to meet customer needs. It is part of NextLabs’ mission to continue to deliver it’s customers value time and time again. We not only prioritize successful solution deployments for each customer, but also place great importance in building long-term relationships with our customers and partners to create great value for our customers.
Our partners bring unique expertise and resources that complement our own, enabling us to deliver exceptional value and drive success for our customers. We are committed to nurture and strengthen our partner ecosystem, ensuring that we always prioritize our customers’ needs and deliver outstanding results.

To meet growing demands and enhance its ability to accelerate implementation of Zero Trust Architecture to bolster cybersecurity for customers, NextLabs has deepened its partnership with Accenture. With this collaboration, they expanded their capacity to deliver Zero Trust Data-Centric Security solutions and continuous data protection to a global customer base faster.
NextLabs has the largest customer base of Zero Trust Data-Centric Security for SAP across public and commercial sectors. Having a 98% customer satisfaction rating, we are one of the most trusted data security companies on the market.
Thanks to our strong partner ecosystem, customers like Solvay, Fiserv, and Boeing have been able to overcome their data security challenges seamlessly.


