Home | Intelligent Enterprise | NIST CSF
NIST Cybersecurity Framework (CSF)
Sustainable approach to manage and reduce cybersecurity risk
Home | Intelligent Enterprise | NIST CSF
Sustainable approach to manage and reduce cybersecurity risk
Created through collaboration between industry and government, the NIST Cybersecurity Framework (CSF), acts as a voluntary framework that consists of standards, guidelines, and practices to promote the protection of critical infrastructure.
Designed to be flexible, repeatable, and cost-effective, NIST’s CSF helps enterprises manage and reduce cyber-risk, as well as foster risk and cybersecurity management communications among internal and external stakeholders. The framework is organized into six core functions: Identify, Protect, Detect, Respond, Recover, and Govern. Each function includes a set of categories and subcategories that provide guidance on how to implement effective cybersecurity practices. It includes a set of implementation tiers that measure an organization’s level of cybersecurity maturity and assess progress towards achieving its cybersecurity goals.
Learn how NextLabs partnered with e National Cybersecurity Center of Excellence (NCCoE) to address the challenge of implementing Attribute Based Access Control (ABAC)
Discover how zero trust principles can be applied to NIST 800-53 to safeguard applications and data from a diverse range of threats
Although the CSF was designed with Critical Infrastructure (CI) in mind, it is extremely versatile and can be used by organizations of all sizes, sectors, and maturities. The NIST Cybersecurity Framework helps enterprises introduce:
The NIST Cybersecurity Framework offers a common language and systematic methodology for managing cybersecurity risk. The framework was designed as a ‘cookbook’ which can offer guidance on how to establish and/or complement an enterprise’s cybersecurity program and risk management processes.
The process of creating Framework Profiles (alignment of the Functions, Categories, and Subcategories with the business requirements, risk tolerance, and resources of the organization) provides organizations with the opportunity to identify areas where existing processes may be strengthened, or new processes can be implemented.
The pairing of CSF Profiles with an implementation plan allows an enterprise to take advantage of the CSF by enabling cost-effective prioritization and communication of improvement activities among organizational stakeholders or for setting expectations with suppliers and partners. Moreover, Profiles and associated implementation plans can be leveraged as strong artifacts for demonstrating due care.
The Implementation Tiers component of the CSF helps enterprises by providing context on how an organization views cybersecurity risk management. The Tiers guide companies to consider the appropriate level of rigor for their cybersecurity program, which can be leveraged as a communication tool to discuss mission priority, risk appetite, and budget.
To learn about NIST’s technologies via its special publications, explore our NIST special publications page.

The NextLabs Zero Trust Data Security helps organizations accelerate their implementation of the NIST Cybersecurity Framework’s six key functions: identify, protect, detect, respond, recover, and govern to manage cybersecurity risks effectively. Using the technologies from NIST’s special publications among its own patented technologies, NextLabs addresses the six key functions as follows:
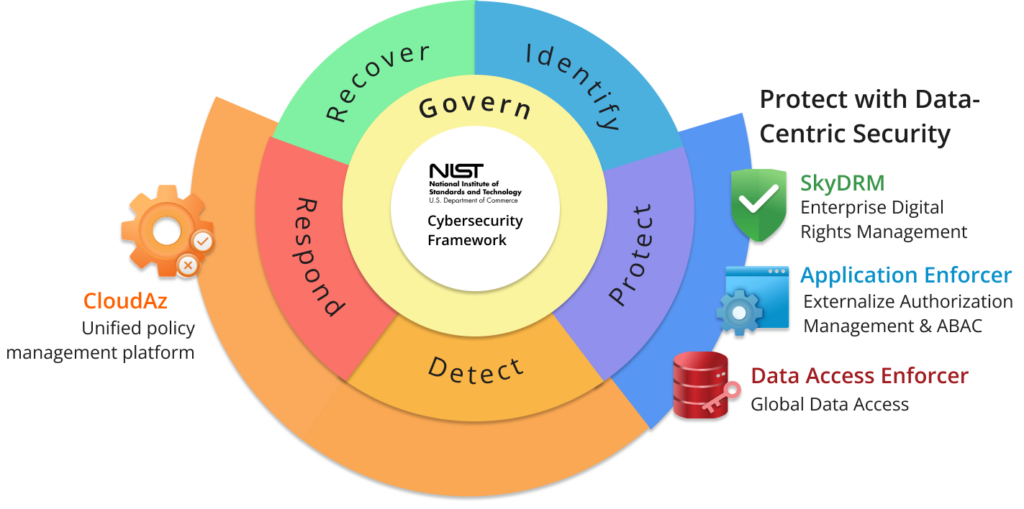
Secure applications, API, & microservices access, externalize entitlement, protect data, & simplify access management
Persistent protection of critical files stored and shared anywhere, cloud payload, and endpoint device
Zero Code Approach to protect data & secure access independent of application with data masking, FPE, & data segregation

Implementation of the NIST Cybersecurity Framework allows organizations to make the transition to intelligent enterprises without compromising on data security. The best practices defined by NIST provide a guide for organizations as they plan their migrations to more digitized operations, and as they collaborate more using shared resources. The framework’s implementation tiers also provide a roadmap for organizations to measure their progress and continually improve their cybersecurity. This structure makes it easier for organizations to implement the changes to become more intelligent than if they had to develop cybersecurity plans from scratch.